Intel has released performance data describing the impact of the Microarchitectural Data Sampling (MDS) chip design flaws announced yesterday.
The “Zombieload”, “RIDL” and “Fallout” flaws revealed yesterday make it possible to infer the values of data, and have been demonstrated to allow an attacker to monitor the websites a victim is visiting despite using the privacy-protecting Tor browser in a virtual machine.
As was the case after 2018’s infamous Meltdown and Spectre attacks, inoculating PCs and servers against the problems can require an update to microcode and/or operating systems. Because the source of Meltdown and Spectre was the way Intel CPUs work across multiple threads, the fixes imposed a performance cost.
Which users did not like one bit, because the exact impact was not immediately apparent and as server users in particular finely tune their servers to drive particular workloads.
Little wonder then that this time around Intel has tested the patches and advised what’s in store.
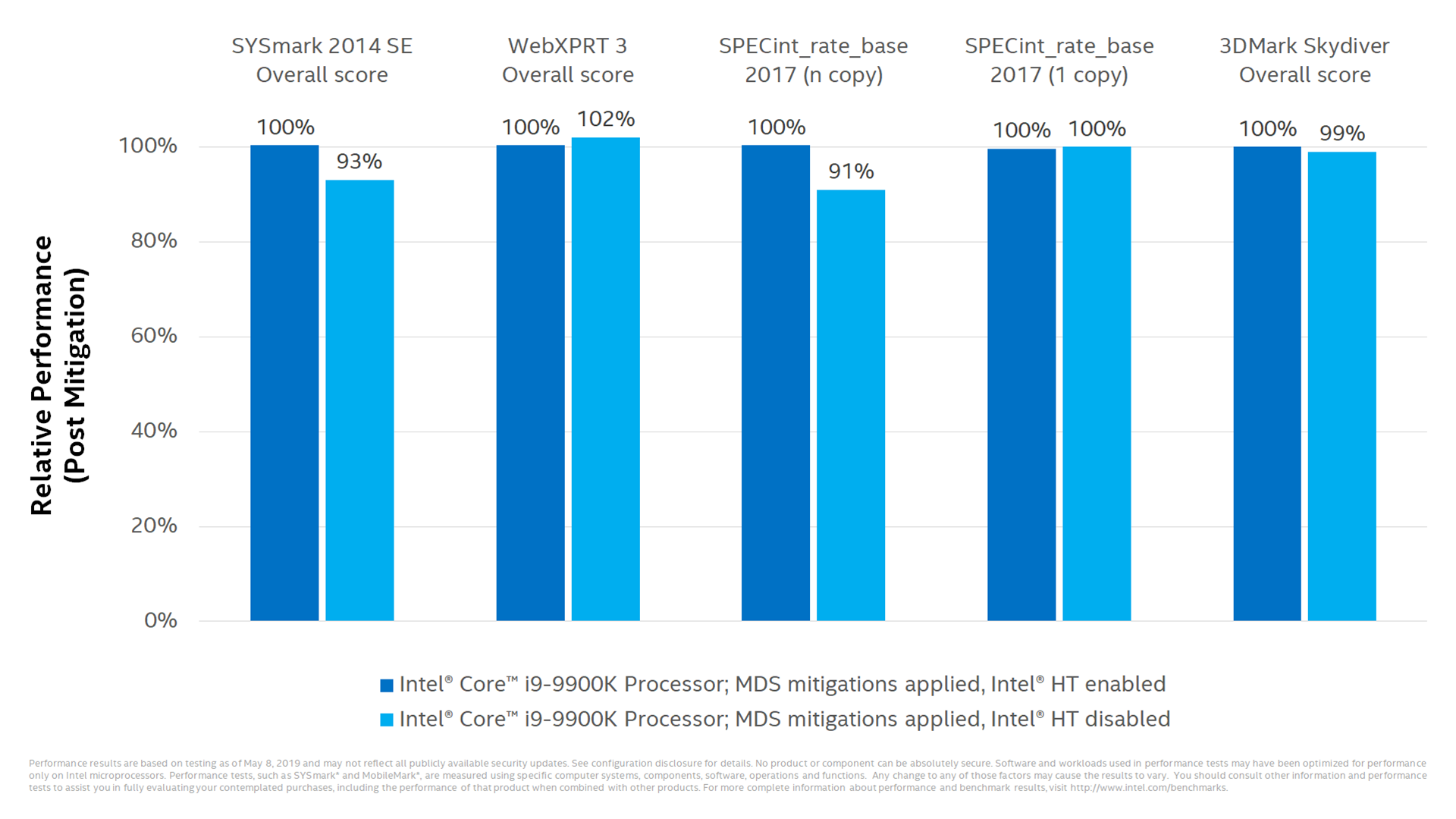
The data Intel has released shows a rosy view, in part because the company has only tested some of the CPUs that have MDS exposure. The company's data offered under the title of "majority of PC clients", for example, evaluated the very high-end Core i99900K and found just a three percent dip under one benchmark - the WebXPRT 3 test - and performance dropped only three percent.
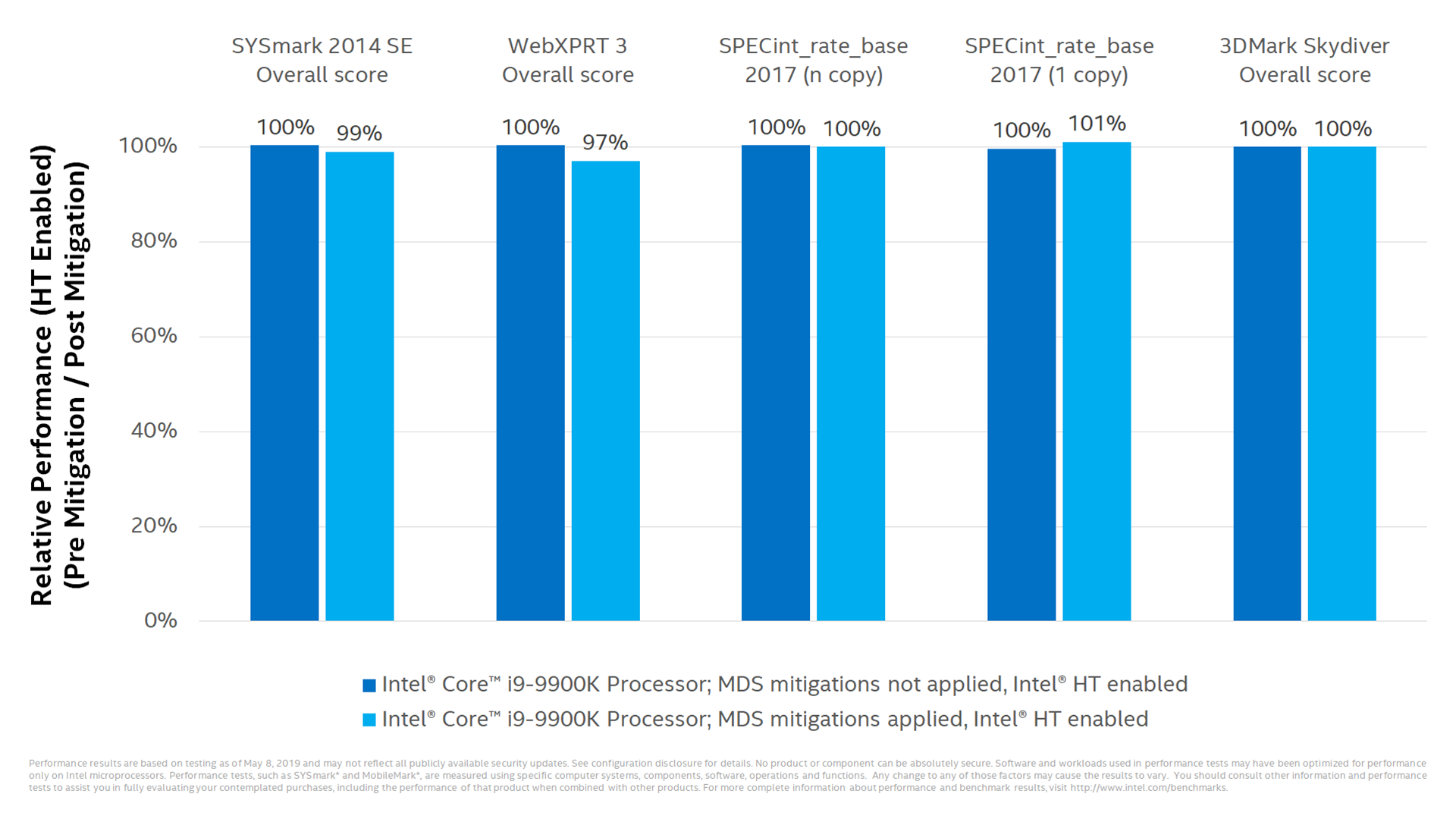
A test of the same CPU with the fixes applied and hyperthreading turned off even resulting in some performance improvements!
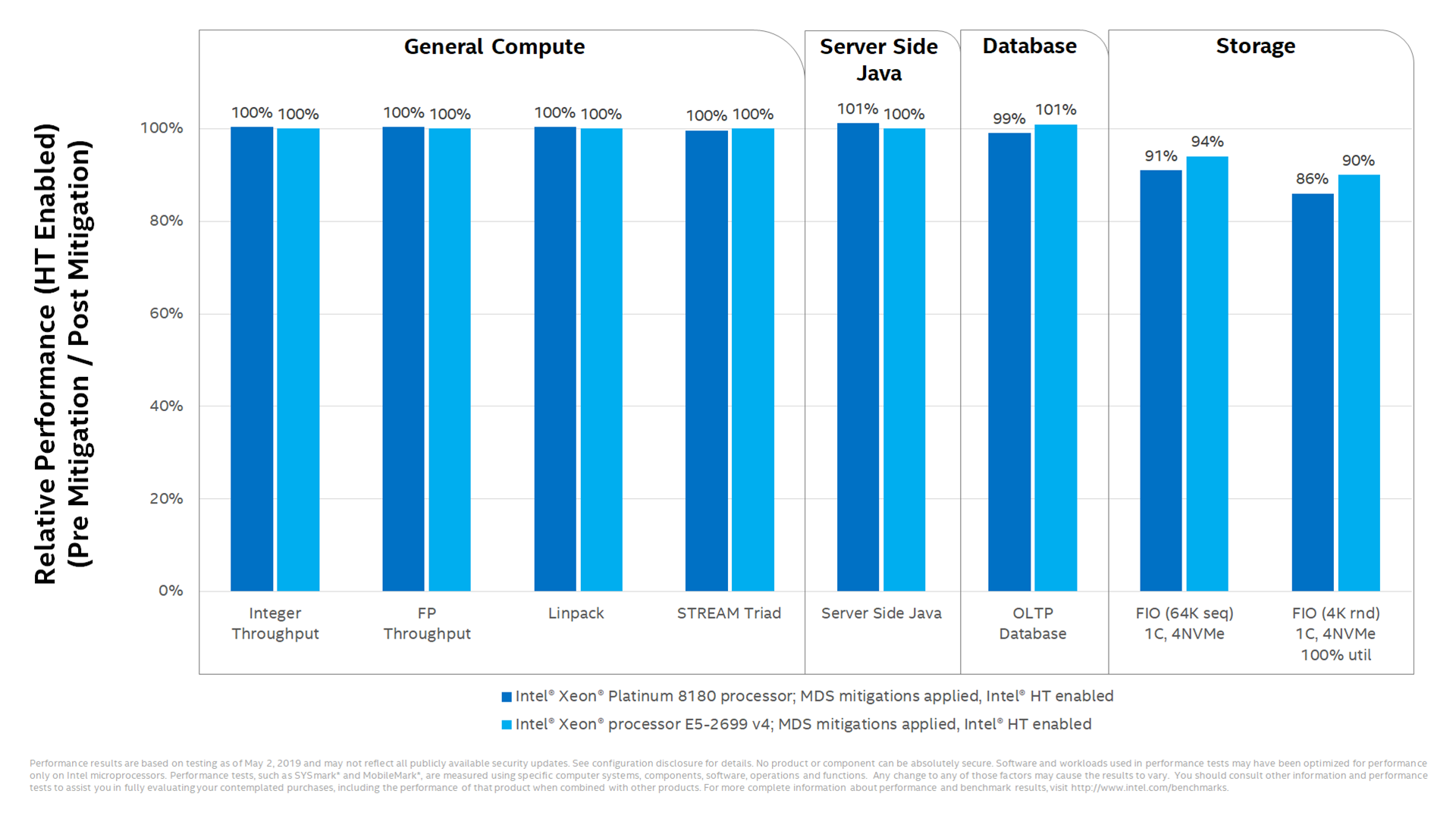
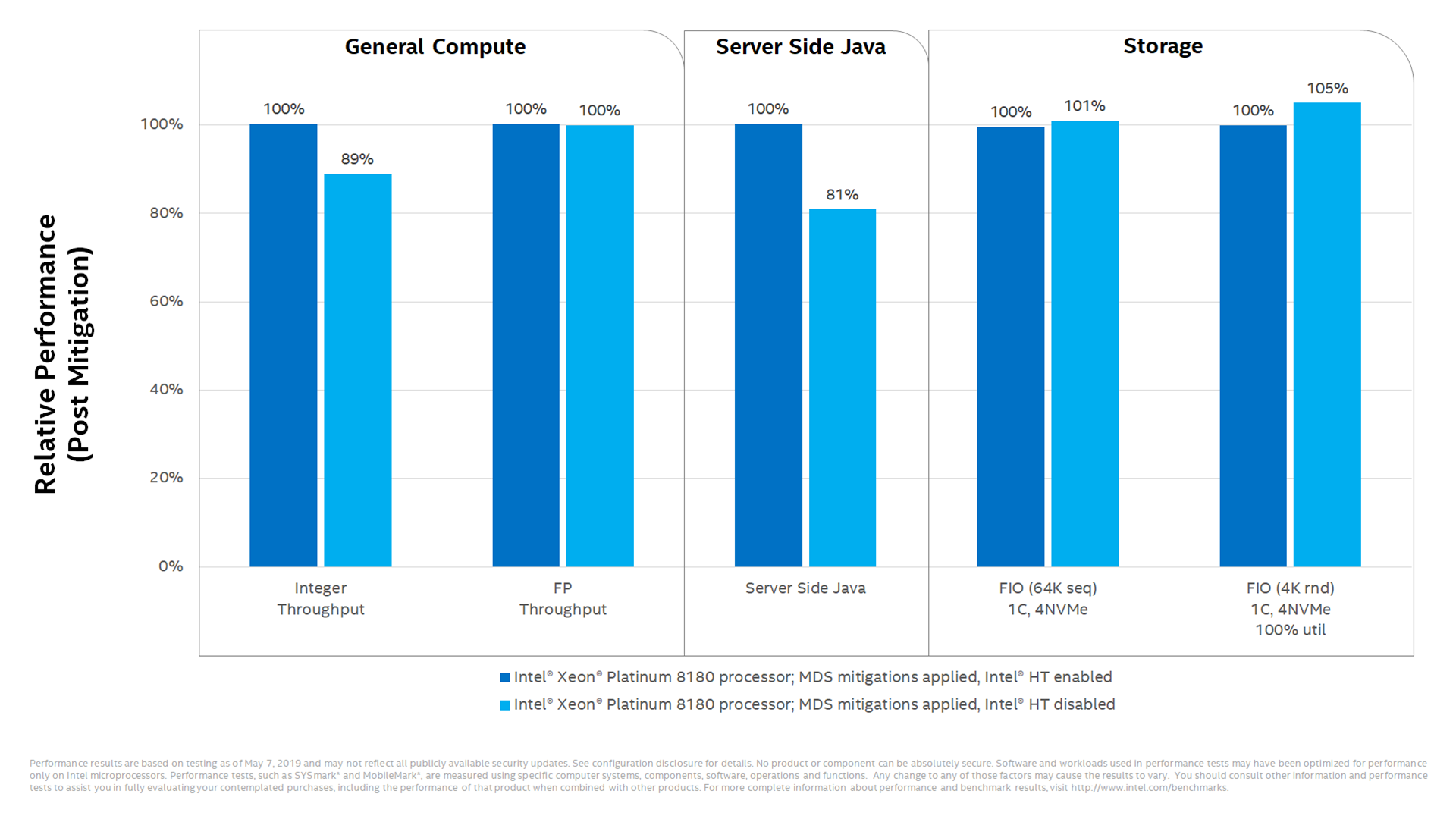
Things are far uglier on the server: the next Intel graphic shows that storage workloads take a big hit.
There's also bad news for server-side Java users who disable hyperthreading.
Intel's page offering these results says that after its latest fixes are installed "it may be appropriate for some customers to consider additional steps. This includes customers who cannot guarantee that trusted software is running on their system(s) and are using Simultaneous Multi-Threading (SMT). In these cases, customers should consider how they utilize SMT for their particular workload(s), guidance from their OS and VMM software providers, and the security threat model for their particular environment. Because these factors will vary considerably by customer, Intel is not recommending that Intel HT be disabled, and it’s important to understand that doing so does not alone provide protection against MDS."
The chip giant's advice also notes that no exploits of the MDS bugs have yet been detected.
The company also sent CRN the following statement:
"Microarchitectural Data Sampling (MDS) is already addressed at the hardware level in many of our recent 8th and 9th Generation Intel Core processors, as well as the 2nd Generation Intel Xeon Scalable Processor Family. For other affected products, mitigation is available through microcode updates, coupled with corresponding updates to operating system and hypervisor software that are available starting today. We’ve provided more information on our website and continue to encourage everyone to keep their systems up to date, as its one of the best ways to stay protected. We’d like to extend our thanks to the researchers who worked with us and our industry partners for their contributions to the coordinated disclosure of these issues.”






.jpg&h=142&w=230&c=1&s=1)

_(21).jpg&h=142&w=230&c=1&s=1)




.jpg&w=100&c=1&s=0)








_(1).jpg&q=95&h=298&w=480&c=1&s=1)


