How secure is iCloud?
Although Apple iCloud came under fire last year when hackers apparently stole photos of celebrities and published them online, this was less a case of iCloud being insecure and more a case of those celebs getting their AppleID passwords compromised through successful phishing attacks elsewhere.
In fact, Apple has a pretty good reputation when it comes to security across its devices, but how does that translate into cloud services?
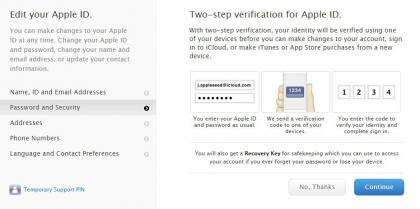
Two-step verification is a must have for any security aware cloud user
The iCloud keychain encryption keys, however, are created on your own devices and Apple can't access them. Apple says it cannot access any of the core material that could be used to decrypt that key data and only trusted devices that you have approved can access your iCloud keychain.
Secure tokens are used for authentication when accessing iCloud from other Apple apps (such as Mail and Calendar) and there is optional two-step verification (which can be turned on at https://appleid.apple.com/account/home) via text message or device generated code for making changes to account information or signing into iCloud from a new device.
How secure is Google Drive?
Google has also fallen victim to the password compromise security scares that impact on so many services. Last year it was claimed that nearly 5 million Gmail accounts had been hacked when a database was dumped on a Russian security forum.
Because Google Drive uses the same Google account for login as Gmail, the danger was that everything was compromised as a result. It turned out, however, that the dump was of old phished passwords and at most 2% may have worked - but were all reset by Google anyway.
One account shall access them all - so securing your login is paramount
In addition, Google offers two-step verification like the other services mentioned here. As for your data itself, this is encrypted in transit (to and from your device, and also between Google data centres) using SSL but only stored at rest using 128-bit AES like iCloud.
Next: How secure is OneDrive and the final verdict





_(27).jpg&h=142&w=230&c=1&s=1)


_(21).jpg&h=142&w=230&c=1&s=1)




.jpg&w=100&c=1&s=0)











