Information about which characters Apple users tap on their iPhones and iPads can be captured by applications serving as modern keyloggers that exploit a newly identified flaw in the latest iOS 7 firmware.
The flaw allows a malicious application to track where users touch on their screens, if they use the Touch ID fingerprint scanner and when the home button is clicked.
That information can then be shipped off to an attacker-controlled server to determine what the user was doing.
Crucially, the flaw affected non-jailbroken devices – stock phones and tablets that had not been modified to remove Apple's security controls – which made it unique among research that focused on applications and techniques that snooped on users operating only hacked Apple products. 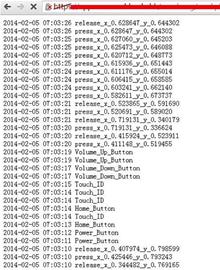
While it was unknown if the tactic had been used by attackers, it presented a potentially greater risk to businesses than attack vectors targeting jailbroken devices that require staff to operate non-modified devices for security compliance.
FireEye researchers Min Zheng, Hui Xue and Tao Wei developed a proof-of-concept application that could slip past Apple's security review process and be loaded onto Apple devices.
"This 'monitoring' app can record all the user touch / press events in the background, including touches on the screen, home button, volume button and TouchID and then this app can send all user events to any remote server," they wrote.
"Potential attackers can use such information to reconstruct every character the victim inputs."
Researchers have contacted Cupertino to help the organisation fix the flaw.
The attack worked against the latest updated and stock iPhone 5s, and also affected older devices operating iOS versions down to 6.0.x.
Hackers could create malicious apps that appeared to Apple to be music programs in a bid to ensure the app continued to work 24/7 on devices.
This researchers said would avoid the chance that users could inadvertently deactivate the app by turning off background software updates via the settings panel.
The music app was not listed in the panel because music would generally be played as a background process.
Attackers could install their wares by disguising it as a legitimate app or by exploiting vulnerabilities in third party apps.
The research released at RSA San Francisco this week came on the coattails of news that malware had been developed to capture user activity on standard Windows phones and tablets and within jailbroken Apple products.
Trustwave senior security consultant Neal Hindocha said that while collecting monitoring intelligence via that proof of concept malware was arduous, it could be retooled to be a slick and automated means of attacking point of sales systems and enterprises.




_(27).jpg&h=142&w=230&c=1&s=1)

_(21).jpg&h=142&w=230&c=1&s=1)





.jpg&w=100&c=1&s=0)
_(8).jpg&w=100&c=1&s=0)











