An infected banner advertisement on the ninemsn web site has been serving up unsuspecting users to the Gumblar malware exploit.
The web site, which is jointly owned by PBL Media and Microsoft, intermittently features a compromised in-house banner advertisement for the 75th anniversary of "Women's Weekly" magazine.
According to ninemsn hosting provider Hostworks, the advertisement did not originate on their systems and was served directly from a Microsoft ad server in the United States.
Users are at risk simply by loading the banner, which silently visits another web page that was listed as a Gumblar Zombie URL (site address) in late 2009.
iTnews approached IT security vendor Websense to analyse the advertisement.
Websense told iTnews that the target webpage is currently inactive but still carries "a degree of risk".
A successful attack would install malware that manipulates Google search result pages when viewed by Internet Explorer.
"Victims may see fake results that will redirect them to fradulent sites," Websense's ANZ senior marketing manager David Brophy explained.
The malicious code also attempts to steal FTP (file transfer protocol) logins and hijack any web sites controlled by an infected PC. Similar attacks were blamed for infections of sites hosted by local hosting company AussieHQ last year.
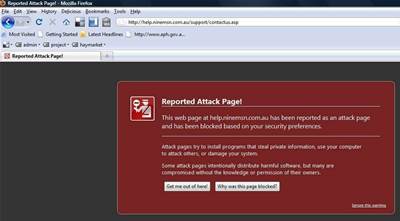
Google has blocked its search engine users from ninemsn's support pages, explaining that the site was listed for suspicious activity three times during the past 90 days.
Google spokesperson Annie Baxter explained:
"Google has set up a number of systems to scour our index for potentially dangerous sites, and we add a label to those that appear to be a vehicle for malware, to protect users who might visit them."
"If a webmaster has indeed removed the malicious content, the warning label will be removed shortly. Our scanners have very high accuracy," she said.
The malware reportedly involved 12 scripting exploits, was distributed by sexsplash.ru and hosted on two domains: jeans-studio.com and condoms.org.ua.
Ninemsn is reviewing the site, following a request for comment from iTnews.
"Ninemsn takes security very seriously and has checks and measures in place to ensure that our site and third party sites that are connected to ninemsn are safe for its audience," a spokesperson told iTnews.
"The instance raised yesterday is a rare occurrence and as soon as it is resolved ninemsn will request that the identified pages are cleared of their warning from Google," she said.
Paul Ducklin, who is the Asia Pacific head of technology at Sophos, told iTnews that the security vendor found no evidence of malware hosted on ninemsn.com.au, and agreed that the Google warning could be caused by a "dodgy banner ad".
"Banner ads which link on to malicious sites are, of course, a bad thing," he said.
It raised the question, he said, as to whether entire sites should be blocked if advertisements posted on the site are serving malware.
"This is a tricky question," he said. "Banner ads can appear almost anywhere on most sites which host ads - so in this case, that would mean blocking all of ninemsn.com.au, even though a good web security product ought to block the banner ads."


.png&h=128&w=207&c=1&s=1)



_(38).jpg&h=142&w=230&c=1&s=1)






.jpg&w=100&c=1&s=0)











