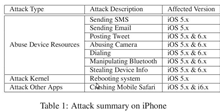
Researchers have developed a backdoored app that can pass Apple App Store security checks.
The new iOS app dubbed Jekyll was uploaded briefly to the App Store wherein it was discovered that the famously security conscious shop had only fleetingly examined the application.
Jekyll, designed by researchers Tielei Wang; Kangjie Lu; Long Lu; Simon Chung, and Wenke Lee of Georgia Institute of Technology, targeted theoretical problems with program analysis including the App Store reviewing process and the code signing mechanism.
“Using this method, attackers can create malicious or term-violating apps and still be able to publish them on App Store, which in turn opens up new attack surfaces on iOS devices,” the researchers wrote in a paper. (pdf)
“We stress that our attack does not assume any specifics about how Apple reviews apps, but targets theoretical difficulties faced by any known methods to analyse programs.”
Jekyll could silently access sensitive devices resources including posting discreet tweets via implicit invocation of private APIs that slipped past the App Review and open a window for attackers to utilise elements of the sandbox restricted kernel space.
The researchers also used Jekyll to issue URL commands, executed by the Mobile Safari web browser, which was then exploited using an unpatched JavaScript vulnerability. From there, the broswer was directed to the JailBreakMe site which busted the Apple device out of its old iOS walled security garden.
"If new vulnerabilities in Mobile Safari are disclosed by other researchers in the future, we can simply take advantage of these new vulnerabilities to launch similar powerful attacks," the researchers said.
To avoid having to submit an explicitly malicious app, Jekyll decomposed its malicious logic into small code gadgets and hid them under legitimate functionalities.
“After the app passes the App Review and lands on the end user device, the attacker can remotely exploit the planted vulnerabilities and assemble the malicious logic at runtime by chaining the code gadgets together."
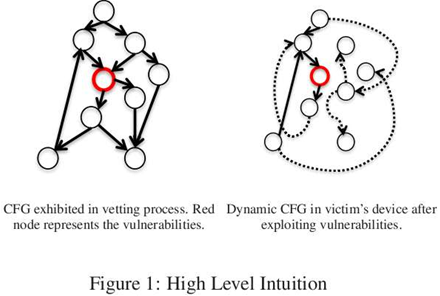
In the figure above, the app's original Control Flow Graph (CFG) on the left was presented to the App Review process in its seeminly benign form while the image on the right illustrates the application during runtime with its new program paths (dotted lines) introduced at runtime by the remote at tackers.
“Since attackers can construct malicious functionalities through dynamically introducing new execution paths, even if the vetting process could check all possible paths in the left CFG, it cannot discover the malicious logic that is only to be assembled at runtime as per attacker’s commands.”
Apple's review process fell short because it focused largely on static analysis, a gap that Apple said it was working to resolve.
"Generally, improving the existing security mechanisms or introducing more advanced runtime monitoring mechanisms can limit Jekyll apps' capability to perform malicious operations. However, completely defeating Jekyll apps is not easy. "







_(21).jpg&h=142&w=230&c=1&s=1)
.jpg&h=142&w=230&c=1&s=1)




.jpg&w=100&c=1&s=0)








_(1).jpg&q=95&h=298&w=480&c=1&s=1)


