|
Credit: XKCD
|
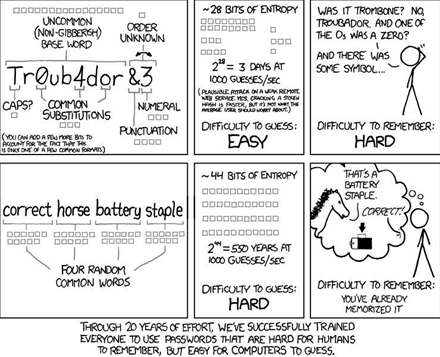
As popular webcomic XKCD notes, the increasingly common practice of substituting numbers for letters in passwords may make the passwords hard for humans to remember but easy for computers to guess.
Strong passwords have high levels of entropy -- a measure of randomness in information theory.
But according to Sophos chief technology officer Paul Ducklin, "humans don't have good entropy" and typically use common phrases that offer convenience but little safety.
“The dictionary approach is problematic because humans don’t have good entropy”, Ducklin says. “Once you have picked the first word, the next would likely have some form of association”.
One such phrase is Benjamin Franklin's famous quote: “They who can give up essential liberty to obtain a little temporary safety, deserve neither liberty nor safety.”
The quote has 557 bits of entropy, making it a good password according to information theory. But it's a poor one in reality, due to its popularity.
To mitigate risks of the dictionary approach, some security experts suggest adding more words, and capital letters or special characters to memorable phases.
One method, known as the Diceware method, uses dice to generate numbers that corresponded to words in a list. It is an attractive offline method that does not depend on crackable algorithms, Ducklin says, but phrases can be hard to remember.
The Sophos veteran is fond of using initial letters of phrases, interspersed with numeric variables. Franklin’s quote using this approach would become "twcgueltoaltsdnlns" and offer 74 bits of entropy -- more if numbers and special characters are used.
Ducklin says numbers should not replace letters in an obvious way, such as 1 for I or 9 for g, since dictionary cracking lists contain such variables.
Neal Wise, director of penetrating testing company Assurance.com.au, uses long, high-entropy passwords formed by number generators.
“I don’t remember many of my passwords because they are so long and complex,” Wise says.
Number generation is another popular method for passwords but is only as secure as its architecture and the complexity of user-picked master passwords.
This dependency was highlighted in May, after online password management system LastPass warned of a possible data breach that did not eventuate.
Generated passwords are also becoming easier to crack thanks to cheap and powerful cloud-computing services. “If you’re leaving security up to Moore’s Law, you’re doing it wrong,” Wise says.
Yet, attackers tend to take the path of least resistance which, in information security, typically involves bad cryptographic hashes and web application flaws.
“Good passwords stored badly – that’s where it all ends up,” Wise says. “If we get the hash, the battle is mostly over.”
Wise often breaks into systems by attacking weak legacy hashing controls underpinning many modern systems. This often goes unnoticed during system upgrades.
Web applications are another target that could undermine strong passwords. They often lack security controls, such as mandatory password resets, minimum password strength and log-in records.
“A big issue is reflecting order and control on web applications," Wise says.
"Apps should tell you the last time someone logged on, be ambigious about whether it was the username or the password that was incorrectly entered, and enforce minimum access attempts before lock out.”






_(27).jpg&h=142&w=230&c=1&s=1)
_(21).jpg&h=142&w=230&c=1&s=1)
.png&h=142&w=230&c=1&s=1)




.jpg&w=100&c=1&s=0)











